Leaked personal information on the internet without the consent of the owner is a recurrent topic in today’s news. This highlights that the companies behind the clouds have security vulnerabilities. According to our research on Google, 49% of the brands have different kinds of security problems which are divided into 5 major categories.
Main Findings
The brand with the problem more repeated on websites is Ring (Amazon), with an ‘Unauthorized access to web, app and system’, in a total of 17 websites. A specific product of the brand, Amazon Cloud Cam, is also in the list of brands with security problems.
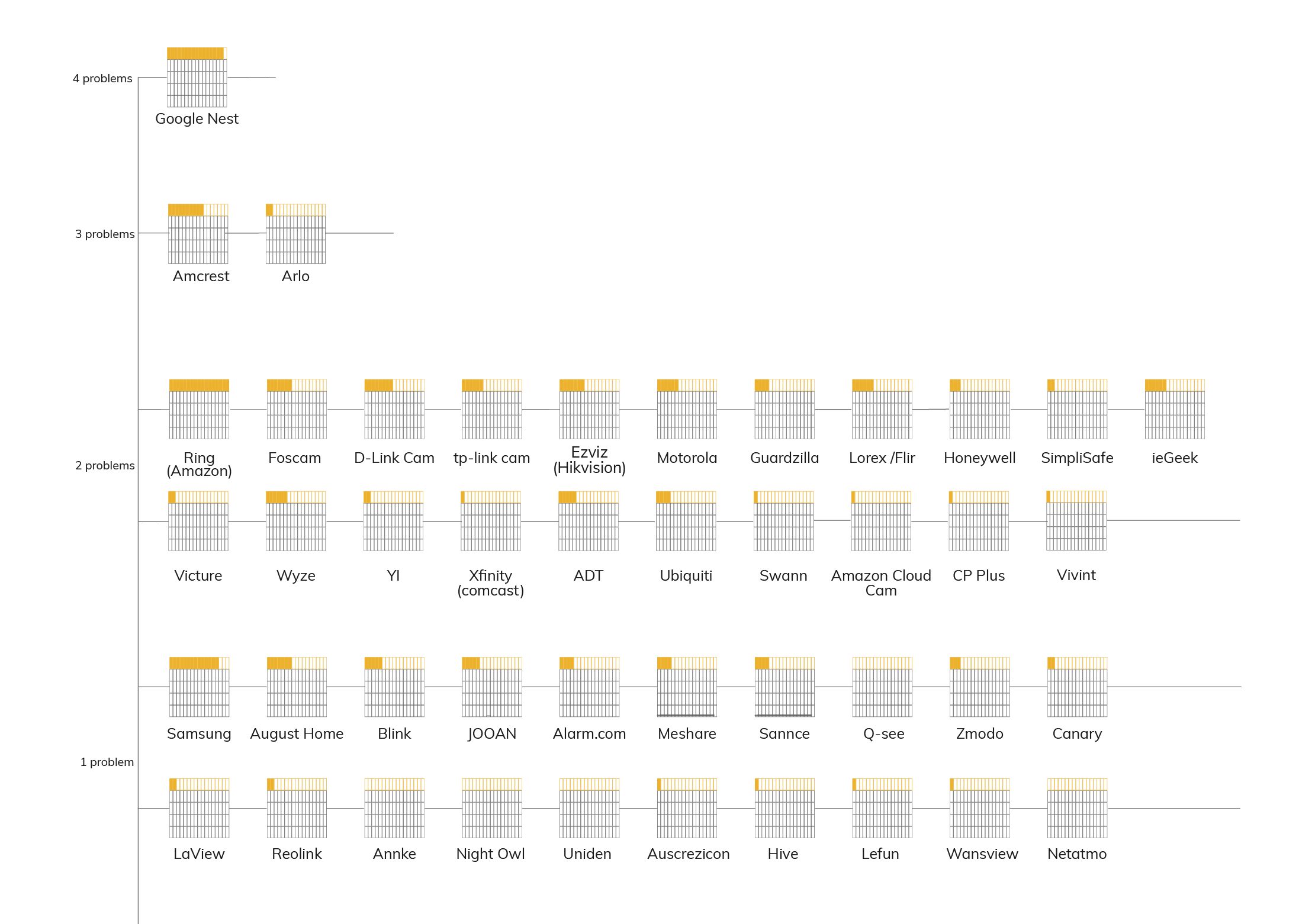
From the first search done in this protocol, 90 most common brands appear in Google results. Almost half of them; 44, had at least one security problem or vulnerability that allows a hacker to access the system.
The brand Google Nest has most scandal stories related to privacy. It faces four types of problem categories. Amcrest and Arlo follow next, each with three problem categories.
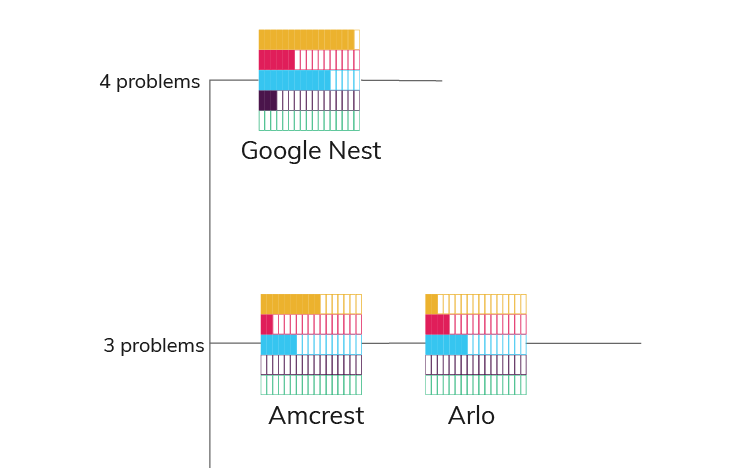
The ‘Easy Credential Access’ shows the cameras that have been accessed because of no or a weak security password to protect the device. It is the second most repeated problem with 20 companies facing it.
Protocol