ABOUT
THE PROJECT
I SEE U is a project developed during the Final Synthesis Laboratory in Density Lab at the Politecnico di Milano.
This project is an extension of protocol 3 from phase II, which highlighted what’s being captured by the most recent cameras on a website called Insecam. During that phase we collected videos from different countries to show the variety between them and the relevance of the content.
I SEE U showcases six different stories of leaked security camera footage found on Insecam, each from a different country. It takes the audience through an informative and interactive journey during which the exact location of the camera is tracked and name and contact details of the place being capture are retrieved. It further provides an opportunity to the audience to contact the camera owner and inform them that their privacy is at risk. The journey ends with a guide that presents a set of tips to make a safer use of security cameras.
AIM, FOCUS AND OBJECTIVE
The aim of this project is to inform the audience, with simple language and real content, that leaked security camera feeds can be easily tracked using simple online tools in just a few clicks.
The project is centered on the use of security cameras and the possible negative consequences of their use. It focuses on a specific audience: existing or potential owners of security cameras and people who are directly or indirectly under camera vigilance.
The main objective of the project is to reflect the vulnerability of cameras that is often more pervasive than expected. People use cameras to feel safe, but paradoxically end up putting their privacy and security at risk. With this project we want to inform, warn and provoke a direct response in the audience.
MESSAGE
Surveillance cameras are becoming part of our daily lives all around the world. How would you feel if you knew that someone can watch you in another country and discover where you live or work? Showing unauthorized access to these videos, the direct message is the vulnerability of these cameras and the ignorance of their possible misuse. How can a security device invert the roles of security and become a window to the personal world?
THE PROCESS AND TOOLS USED
The entire research and execution process has been carried out manually. We picked six camera streams from different countries and locations such as a bar in Italy, a motorcycle shop in France, a fast-food restaurant in the USA, or a convenience store in Brasil. We created a video for each one to document the process of tracking these cameras.
First, we observed the cameras, analysing them and looking at specific details that led us to find the location.

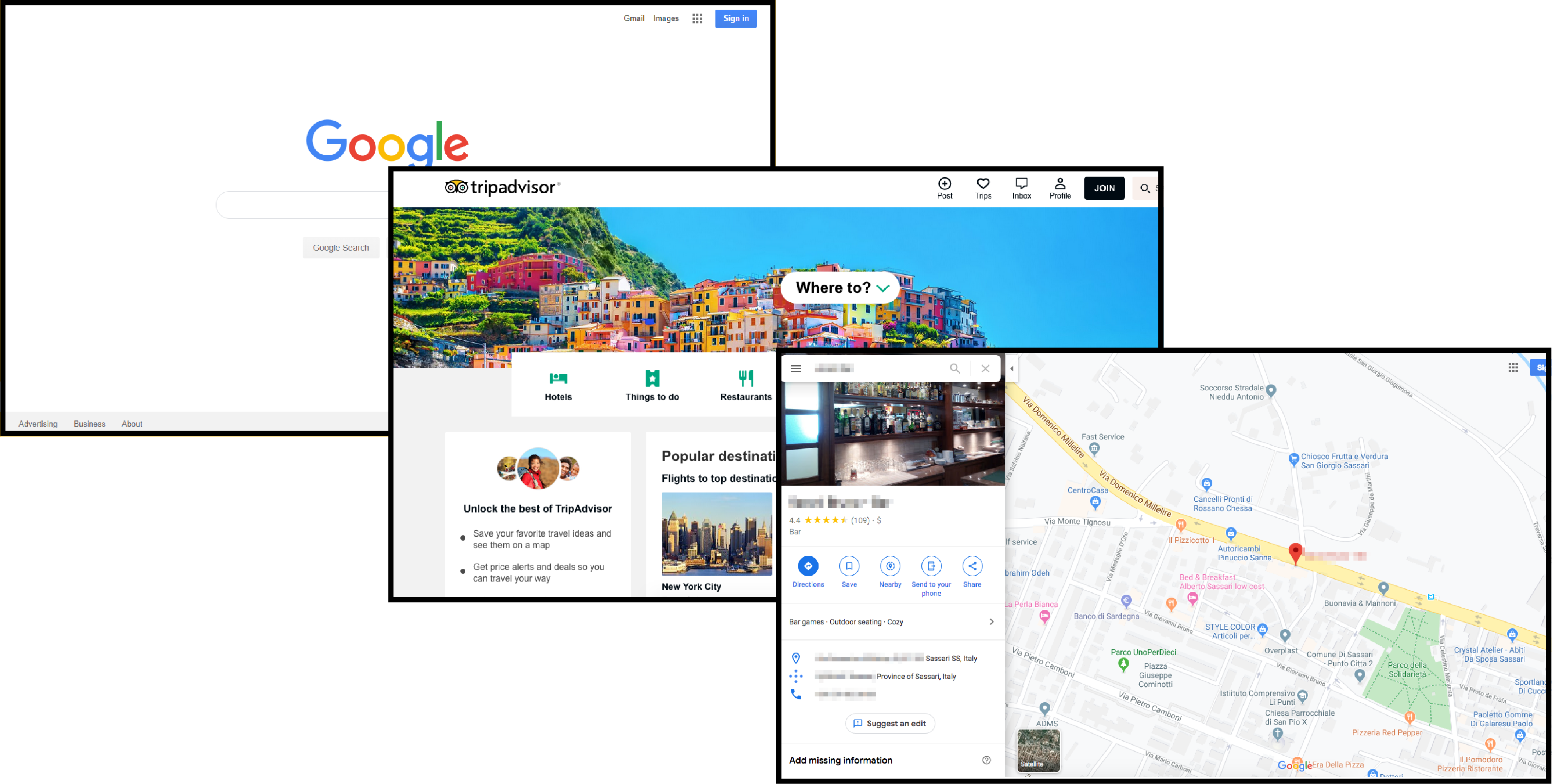
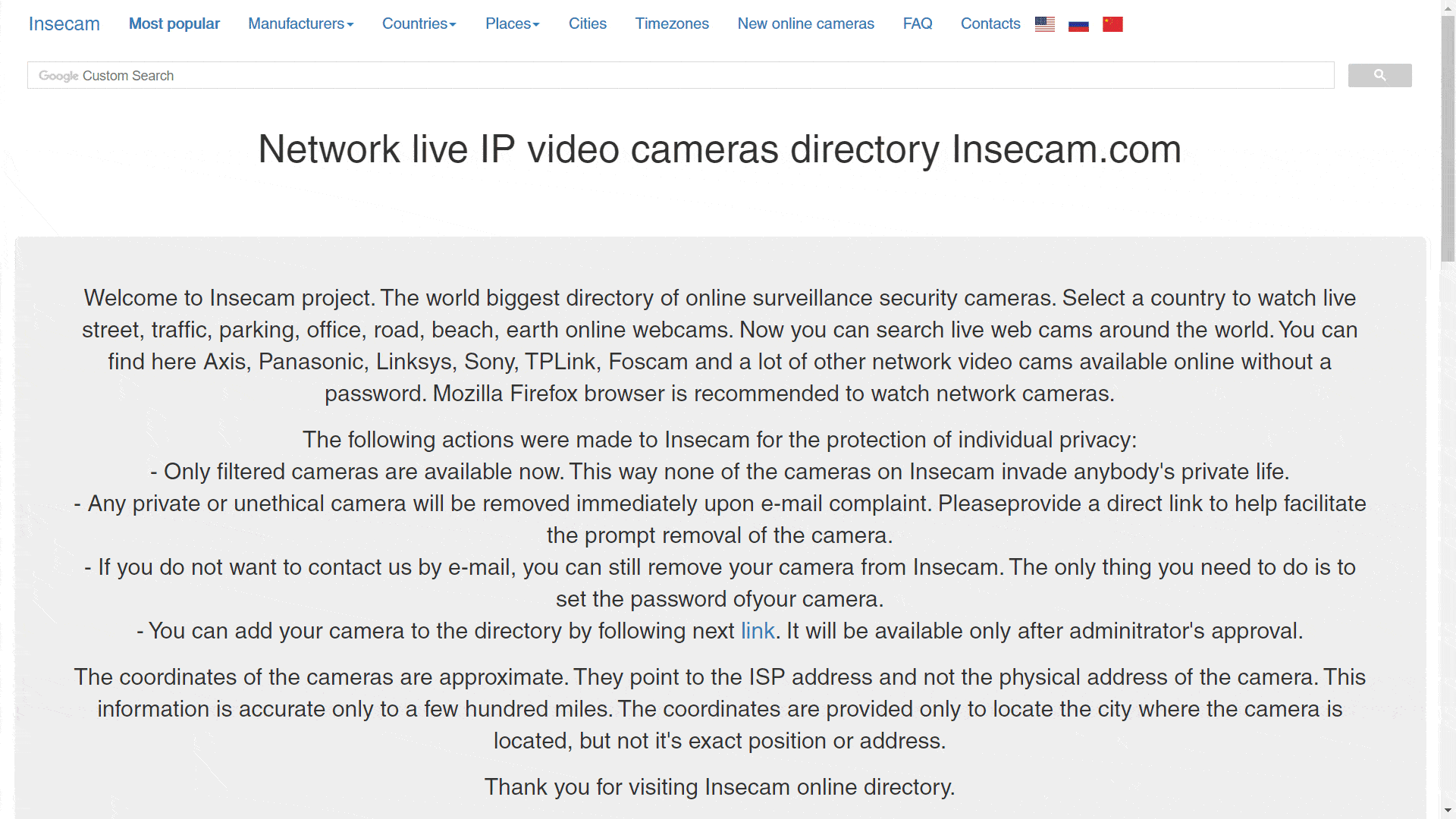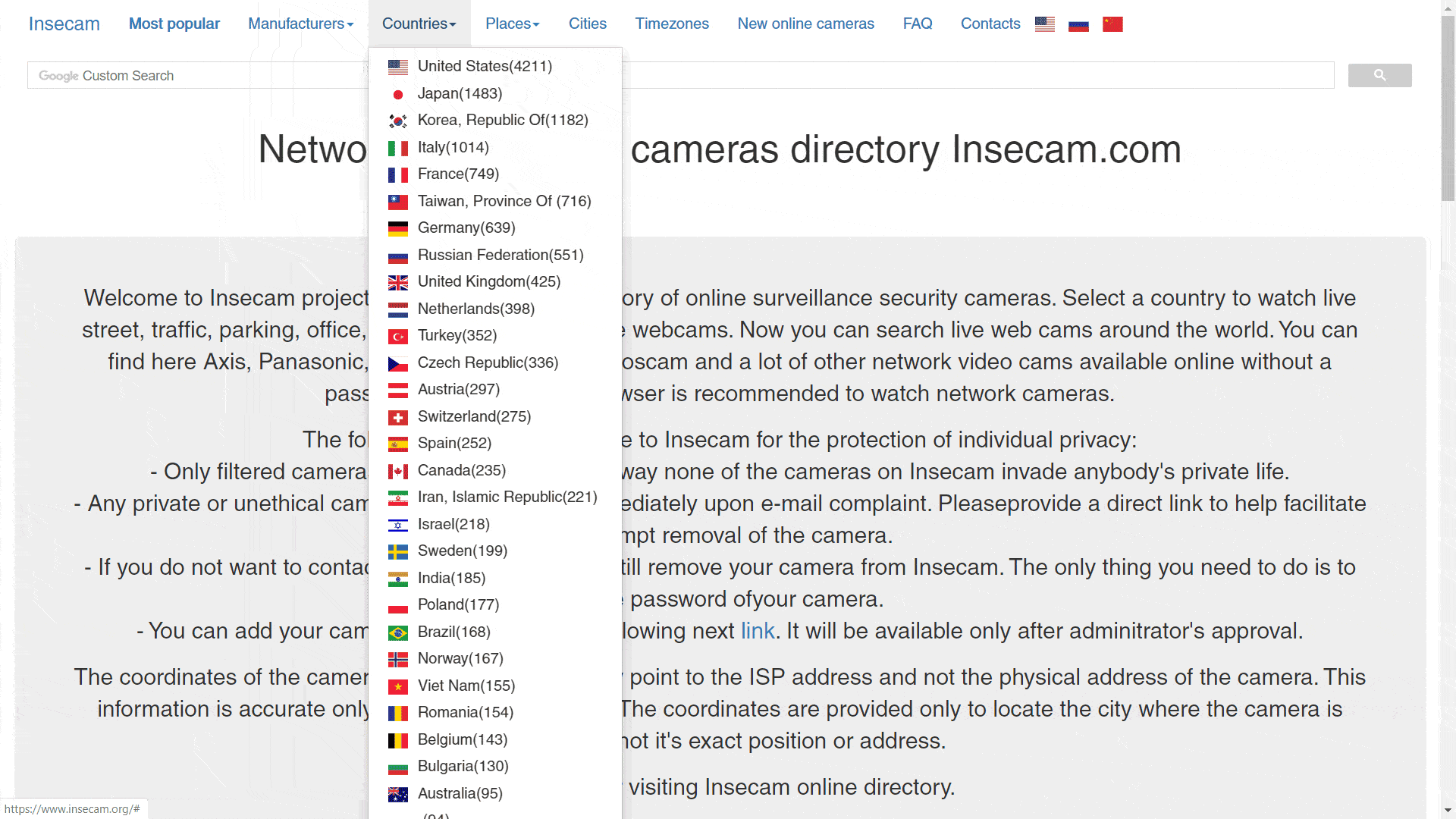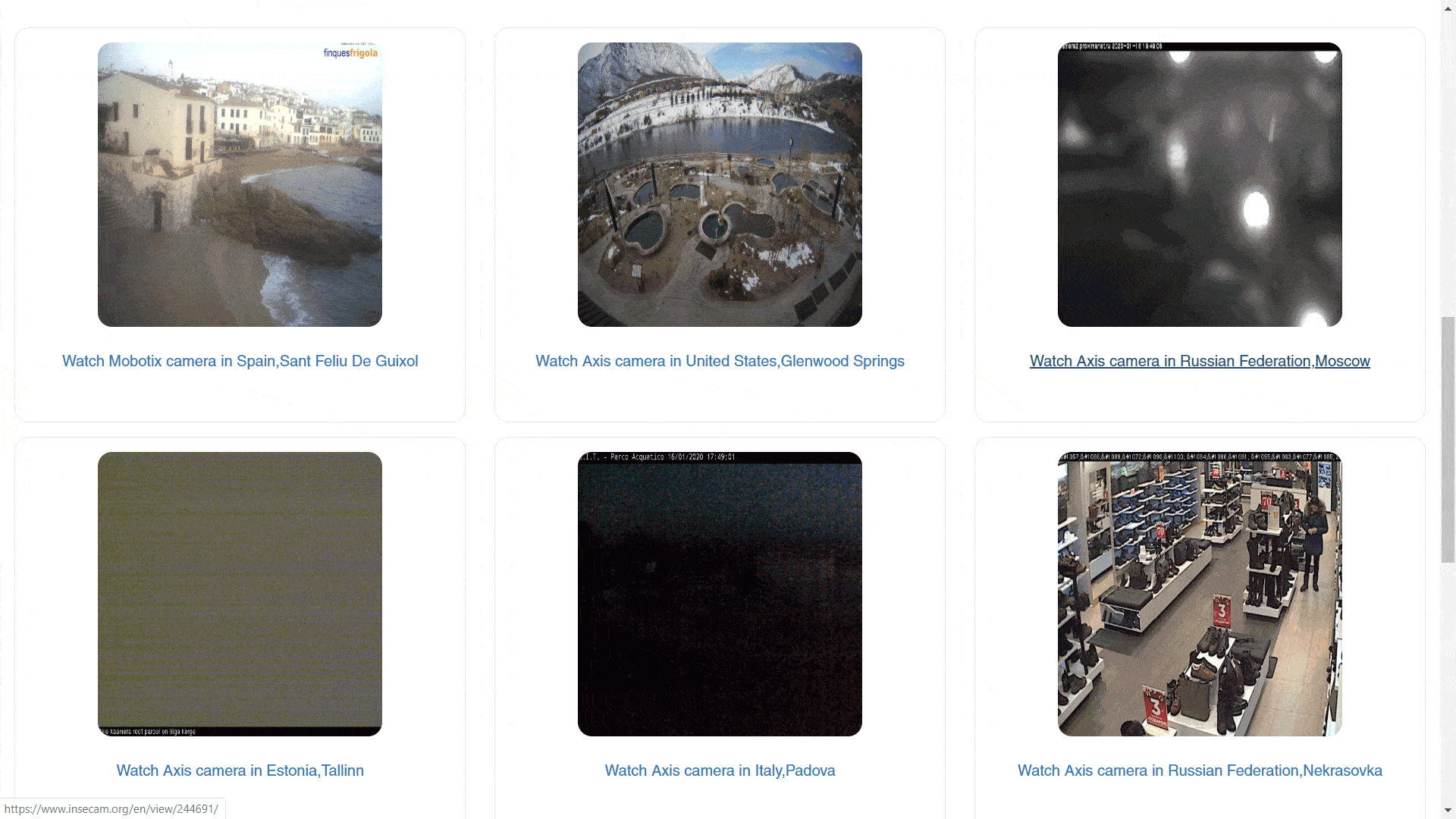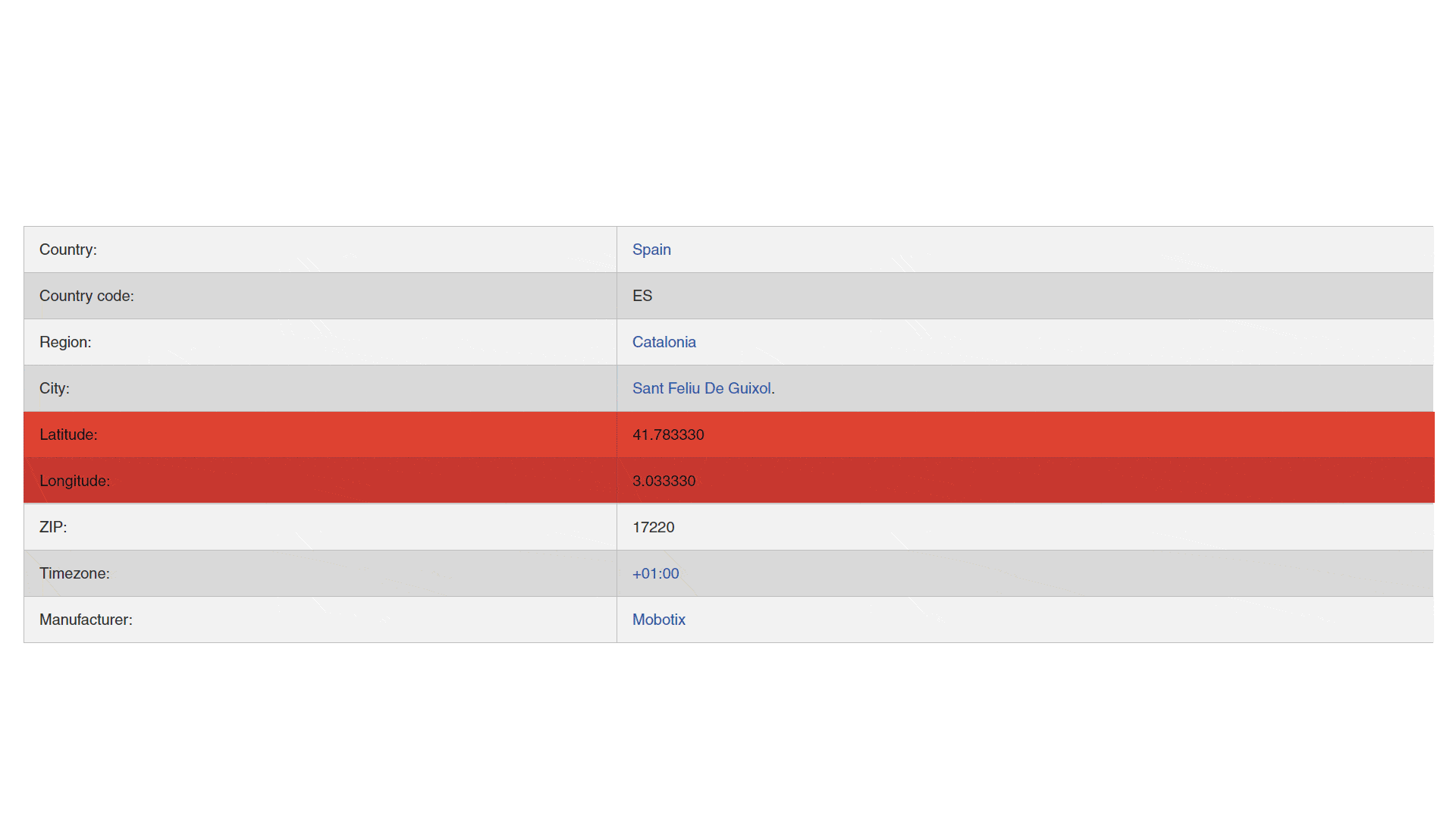
We used platforms like Google Search, Google Maps, TripAdvisor, Facebook and others to obtain supporting evidence of each location and to further re-check the correct address. Through the exact location or name
of the place, it becomes very easy to obtain their contact information online.
With a single search it was possible to obtain all the data of the place, including opening hours, telephone and also pictures, that often helped or allowed us to confirm the location.
After obtaining the phone number, we decided to call them to confirm the camera location and to inform that there was open access to the camera. As different countries were chosen, the calls were made in the local language of
each location, with added English subtitles in the videos. It is interesting to note the different kind of responses and reactions that people have to the situation.

Some are shocked or frightened whereas some think this is a prank and hang up the call. These reactions resonate with the fact that the people were unaware of this situation and that it therefore requires urgent attention.
During some steps of the videos, the user is asked if they want to proceed watching the video or to exit it on behalf of maintaining people’s privacy.

Changes were made on the audio of the calls to protect the anonymity of the person in cause. At the end of each process video, there is an explanation of the main reactions during and/or after the phone call and a feedback, a week or longer after, disclaiming if the camera was or not still open to access.
Sassari, SS, Italy | Buenos Aires, BA, Argentina
Billy-Montigny, HDF, France | Gastonia, NC, USA
Erechim, RS, Brazil | Oviedo, AST, Spain
VISUAL LANGUAGE
The digital language is reused in a very simple, real and raw manner that helps the audience to actually experience a real life situation. For example, exact shots are taken from websites like Google Maps and Trip Advisor.
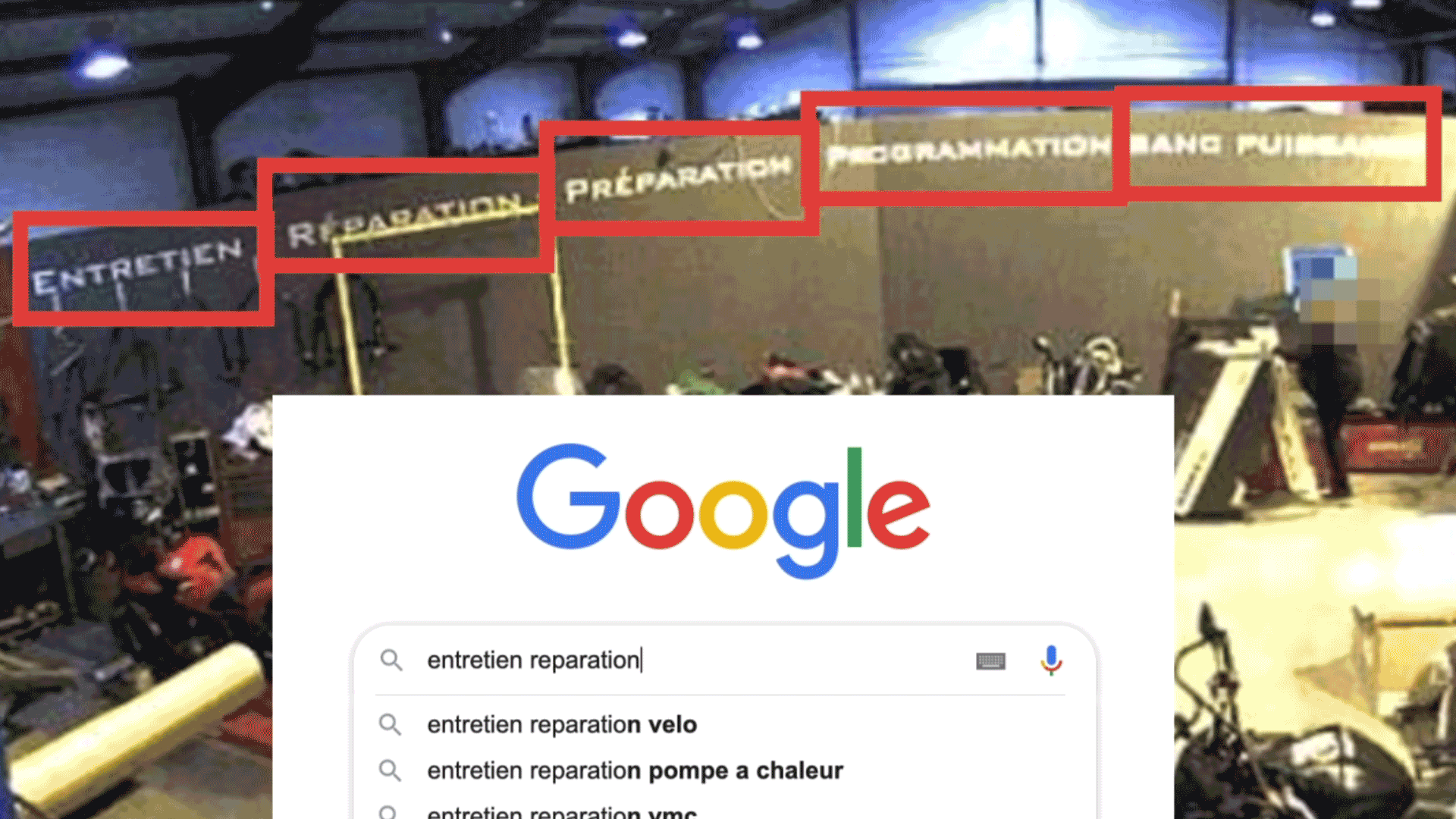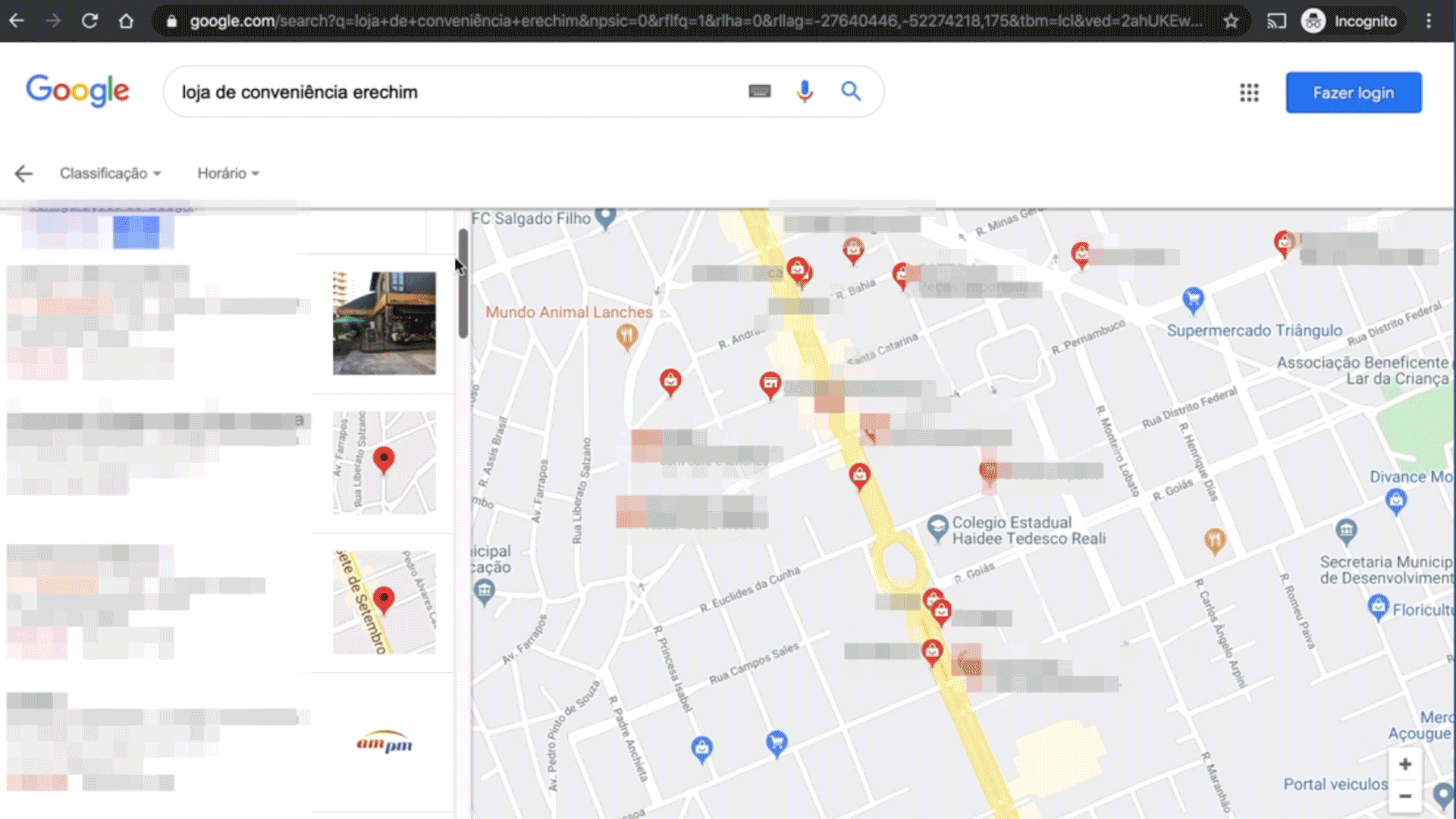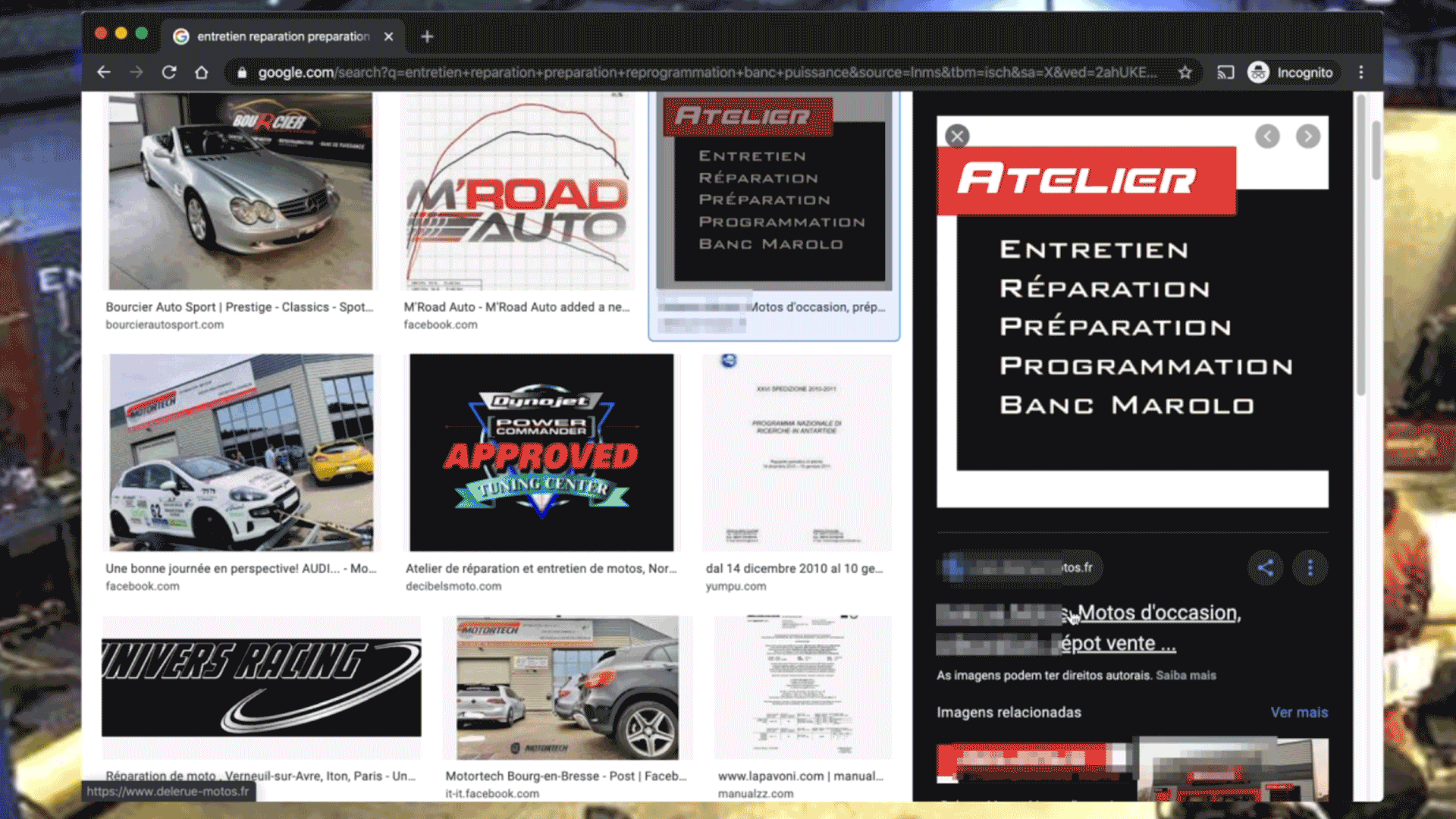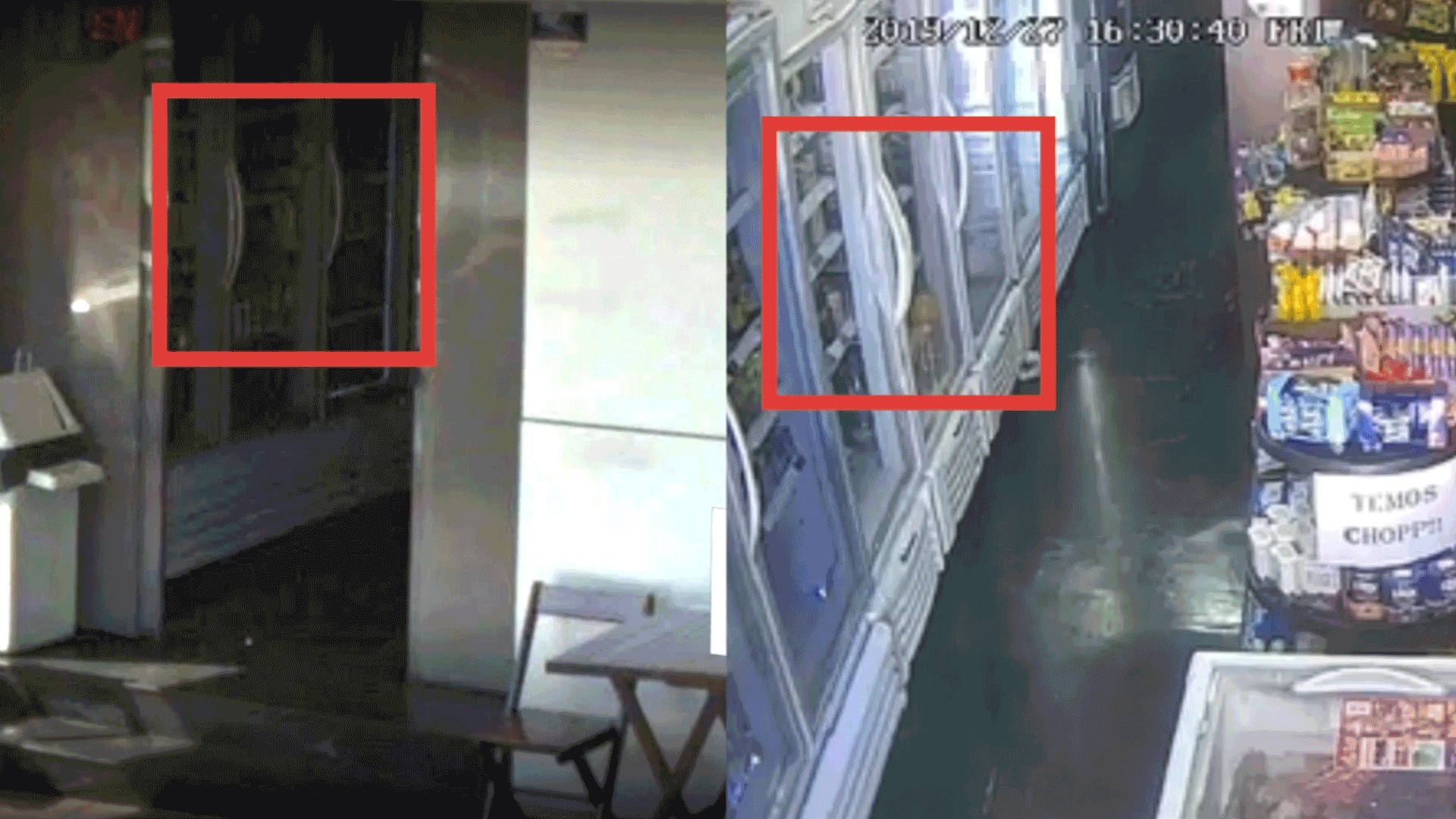
It provokes a feeling of taking proactive measures to prevent unauthorized access of security cameras. Sound effects are an important part of the project. It makes it interesting and provides a real feel to the audience.
The combination of data, visual, text and interaction helps the audience to be more conscious about privacy concerns and acts as torchbearers to spread awareness.
DATA SOURCE
Insecam, is an online directory of surveillance security cameras. It displays unsecured cameras from all around the world categorized by location, country, city, popularity or tags. These cameras are either streaming on publicly accessible network ports or are still using the default passwords, thereby allowing anyone to gain access to the stream. One can easily see the live feed of these open cameras as their brand, latitude and longitude (IP address of security camera).
The material shown in the project has been collected and edited directly for us. It’s possible to access to the videos here. The data regarding the
website is available here.
INTERACTIONS
In the main page, it’s possible to choose between the six different camera stories and decide with which story to begin. Moreover, when the story is finished, it’s possible to go back and watch the other ones.
At various steps the audience is given the possibility to either keep going deeper in the data breach or to opt out. The idea is to actively involve and engage the audience while transmitting the idea of doing something that is "not allowed" due to its disrespect to other's privacy. This rhetoric of breaching others privacy enforces the message yet in a cautionary way.

After the last video of the research process, we present to the reader the possibility to call to the camera's owner. By making the audience feel that they will be able to contact the camera owners, we present a set of suggestions on how to proceed in this kind of situations during the call.
This step is an attempt to make the audience feel more engaged with the project, suggesting even the possibility to call to another cameras owners to warn about the breach. It is followed by suggestions to make sure that the
audience convey the message to the security camera owner in the best way possible, preparing the readers to spread awareness regarding to security cameras vulnerability. By doing this the message is reached and absorbed by both, the
audience and the camera owner.

At the end, we present our last video, that provides a phone call made by us to the respective owner or employee of the establishment where the leaked camera was present. The edit of the call was made due to privacy reasons.
SECURITY GUIDE
In order to further inform the audience against unauthorized access of cameras, we developed a list of security advises to prevent this situations. Simple tips as putting a strong password or to not use the one that comes by default, can reduce the risk of data breach and security.
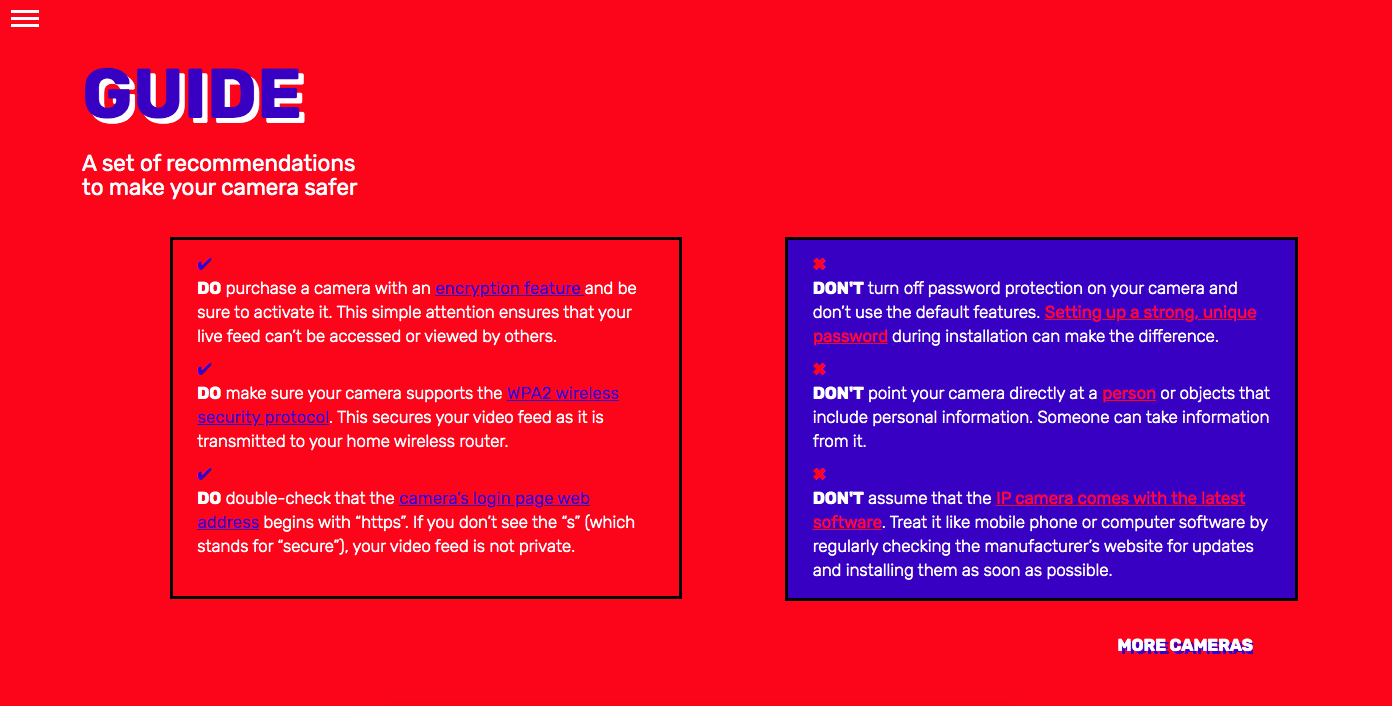
This guide will appear directly when the video of the call finish, allowing the audience to check the best ways to protect their cameras.
A PRIVACY NOTE
During the entire project sensitive contact information and facial images were retrieved. The privacy of parts involved was protected, for example, by pixelating/blurring contact details or faces and muting voices.